News Story
PUF-based key holds promise for IC security
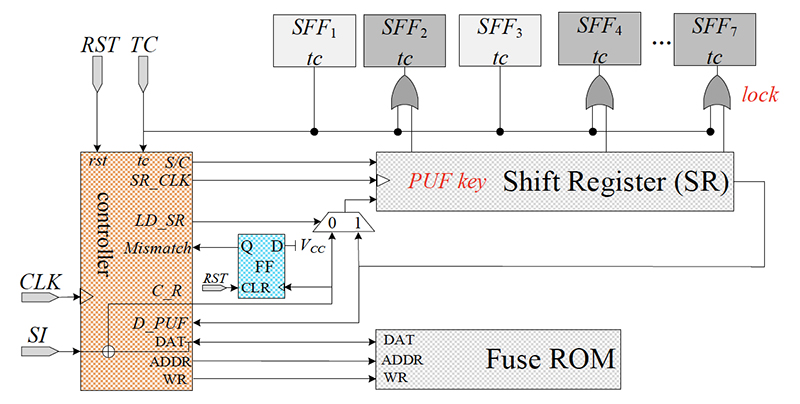
A secure scan design with PUF response as the key.(Fig. 2 from the paper)
Testing is indispensable in integrated circuit (IC) manufacturing to guarantee a satisfactory yield. To facilitate testing, “scan-based design-for-testability” IC design structures have been widely adopted. Full-scan design provides the circuit under test with high testability.
The drawback is that this kind of design provides a side channel that allows a user to access the internal states of chips. In what is known as a scan-based side-channel attack, attackers use this channel to deduce cipher keys involved in cryptographic chips.
Many countermeasures against scan-based attacks have been proposed to authenticate users before the scan chain can be used for testing. Such countermeasures usually adopt a lock and key scheme in which a “lock” is inserted around the scan chain. Without the correct key, users only observe erratic data from the scan chain.
But how can the security of the stored correct key be guaranteed, and how can a key be shared securely among chips with the same design? These concerns have become an obstacle to the application of a secure scan design scheme.
Physical unclonable function (PUF) has been widely investigated as a potent security primitive for ICs. PUF designs transform the intrinsic random variations in device parameters, such as threshold voltage Vth and channel length Leff, to variations in circuit-level parameters (e.g. current and delay). Such transformation can typically construct a set of unique and random challenge-response pairs (CRPs) for a chip. A random key can be derived from a digital response from the PUF design triggered by a digital input as challenge.
At the 2020 IEEE 38th VLSI Test Symposium (VTS), Professor Gang Qu (ECE/ISR) and his colleagues presented research on a New Secure Scan Design with PUF-based Key for Authentication. Qu’s co-authors are Qidong Wang and Aijiao Cui of the School of Electronic and Information Engineering, Harbin Institute of Technology, Shenzhen; and Huawei Li of SKLCA, Institute of Computing Technology, Chinese Academy of Sciences.
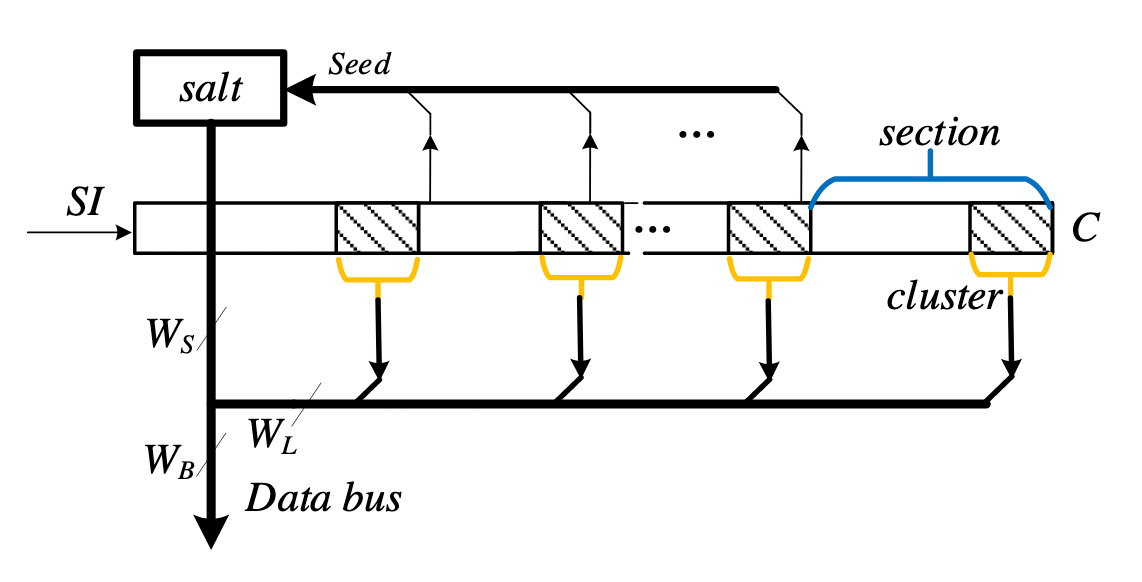
Their research proposed a new secure scan design scheme with a unique PUF-based key for each design, to provide authentication and alleviate the security concerns about the key. In their new “lock and key” scheme, the scan design only can be used normally when a user inputs a key which matches the PUF-based key. The researchers introduce a shift register to implement the authentication of the input key that can be reused as a delay-based PUF design for key generation. The uniqueness of PUF guarantees that each chip can have a unique key to unlock the scan design.
Once the PUF is invoked for the first time, the PUF response is hardcoded into the design so that even if the environment changes, the PUF-based key is maintained. The secure scan design with PUF-based key can protect cryptographic chips against all known scan-based side-channel attacks while incurring negligible overhead.
Published June 24, 2020